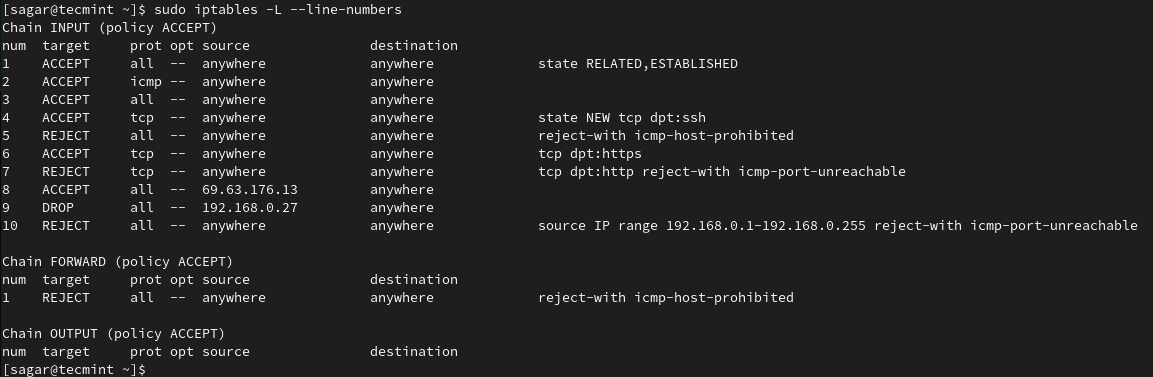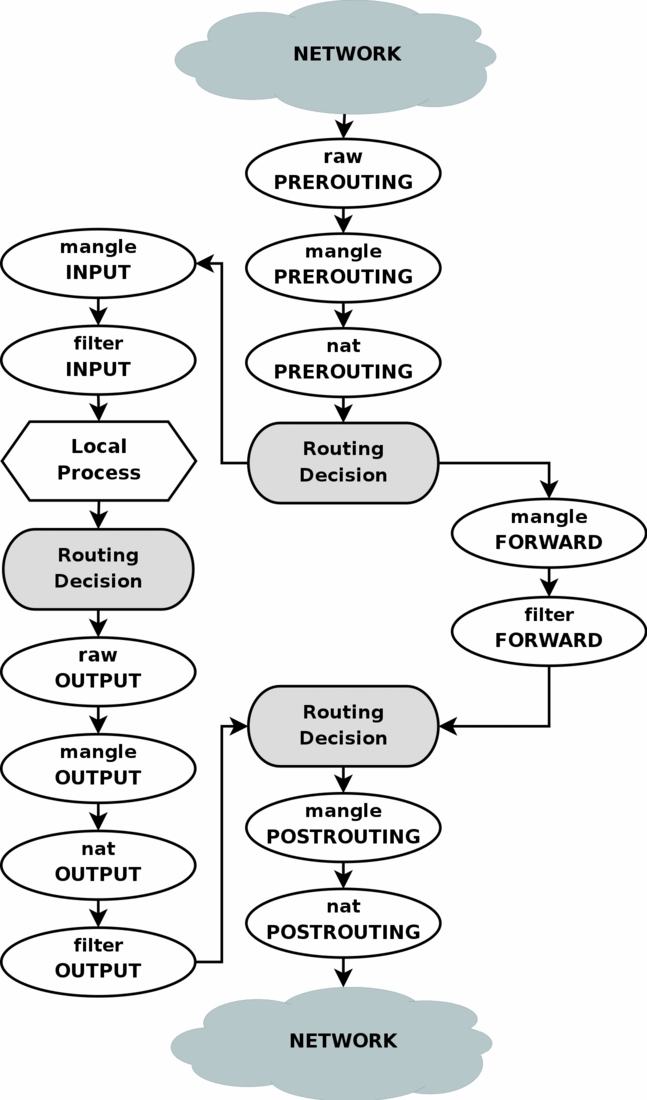
An Extraordinary Network Setup Where You Can ping to Google but not to Facebook From the Same System - DEV Community
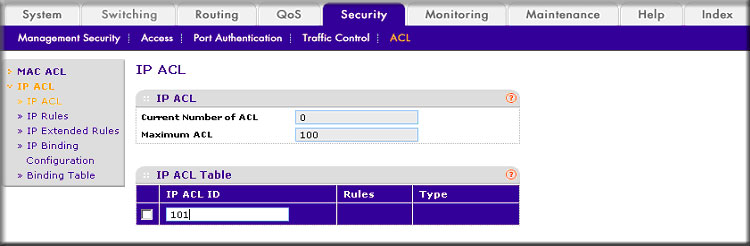
How do I set up an IP Access Control List (ACL) with two rules using the web interface on my managed switch? - NETGEAR Support
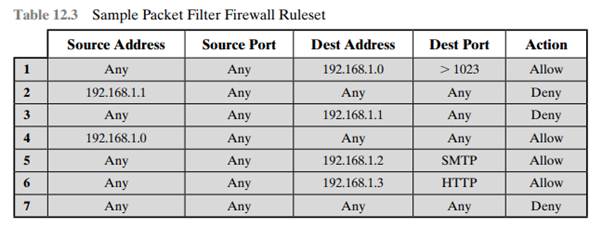
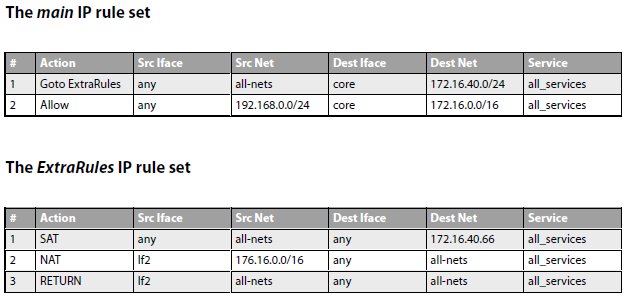
Solved) - 1. Table 12.3 shows a sample of a packet filter firewall ruleset... (1 Answer) | Transtutors

security - Messed up IP table rules and locked myself out while setting firewall on SSH - Unix & Linux Stack Exchange
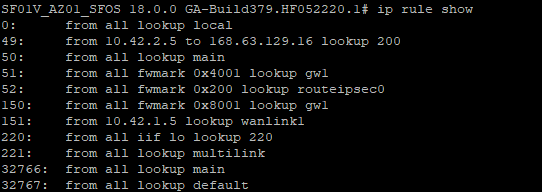
Sophos Firewall: Implement a full HA (inbound/outbound) on Azure - Recommended Reads - Sophos Firewall - Sophos Community

Table I from Automatic detection of firewall misconfigurations using firewall and network routing policies | Semantic Scholar
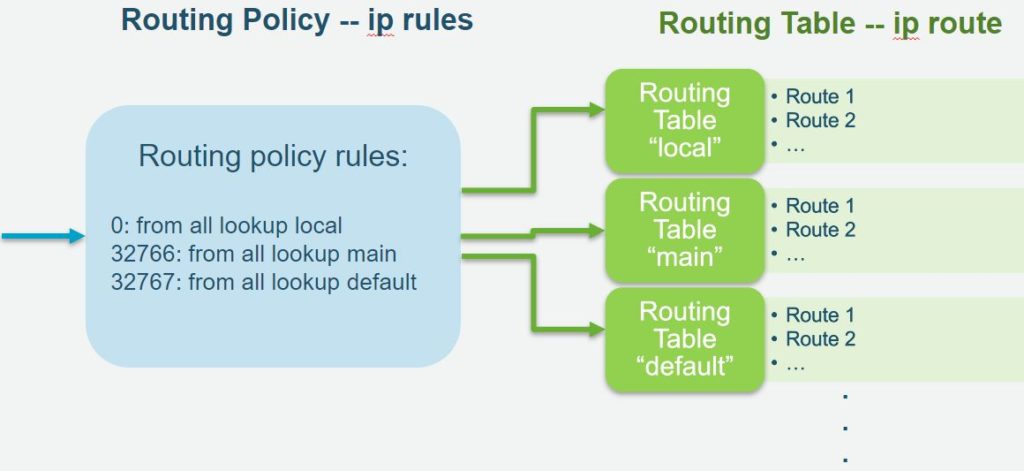
What's Asymmetric Routing? Dealing with Two ENIs and Asymmetric Routing on AWS EC2 Linux instances - 派瑞練習曲 Perry's Etude